
Zero-knowledge age verification proves users are old enough without exposing personal data. Privacy-first compliance for websites - no surveillance, just proof.
Overview:
Introduction - Age Verification as Part of Digital Identity
The growing incidence of the digital ecosystem renders the digital identity as an essential component for secure and seamless transactions. Access restrictions are important across most of the digital domain. With the ever growing significance of digital interactions, or be it various government measures linked together with a common identity, the restrictions and permissions to access digital media are becoming ever more important.
Digital Identity at its core also includes age verification in a very large number of use cases. Most of the validations related to a digital identity solution have valid age as a basic underlying criterion. This aspect is crucial for the successful execution of the digital Identity mechanism as there are a lot of real-life examples where users are provided or restricted access based on their age. Hence, it is crucial that the digital Identity solution is able to accurately and seamlessly provide the confirmation of the User’s age. Regulators across the globe have acknowledged and acted on this topic. KYC in banks or eligibility to government subsidies or application of SIM cards with a telecom operator to name just a few, each has age verification as an underlying criterion, along with others, to provide an affirmation or otherwise to the verifier for further action.
Hence, age verification should be considered as a specialized and integral part of the digital Identity mechanism.
In this article, we will share a point of view on whys and hows of age verification.
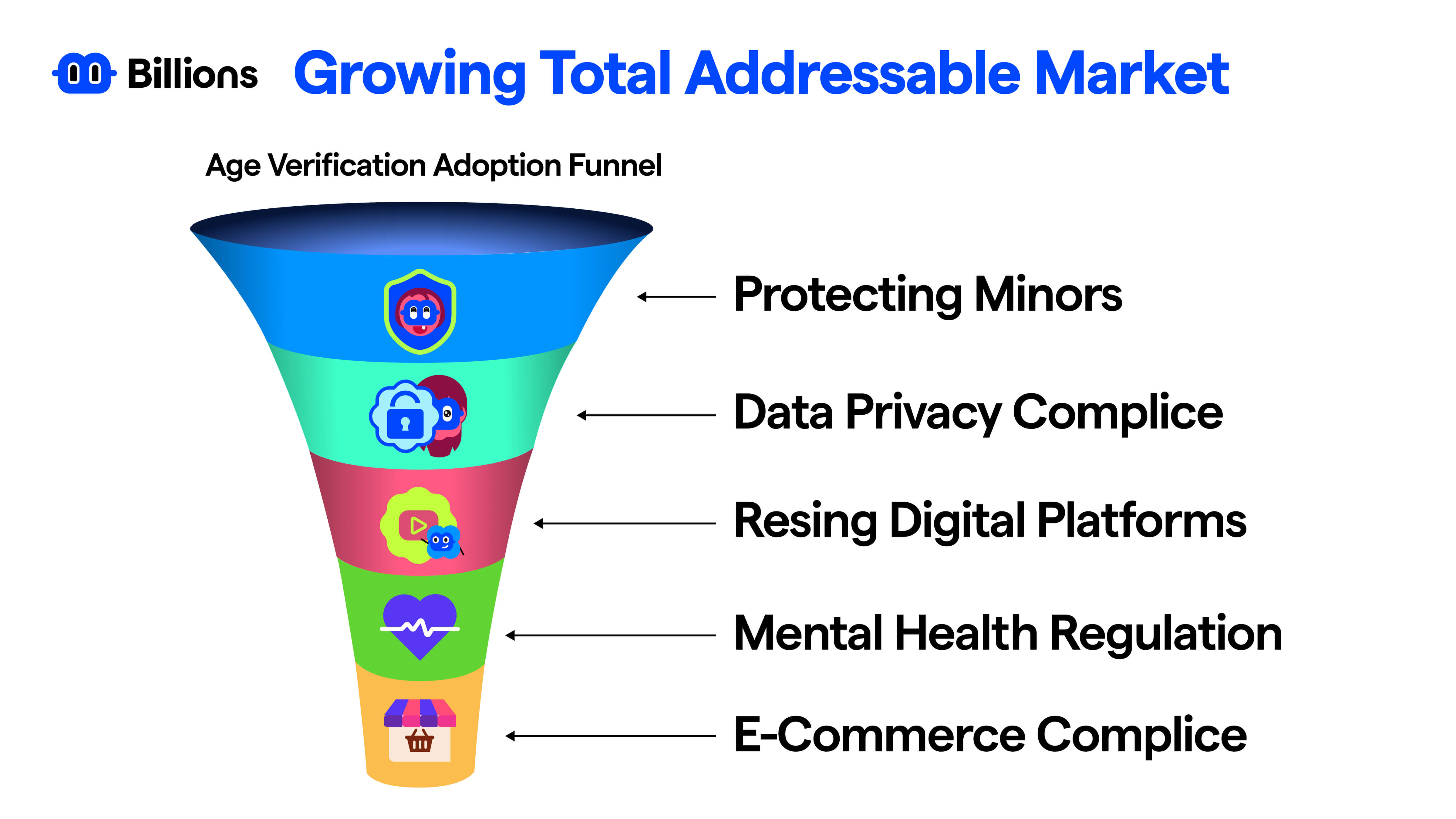
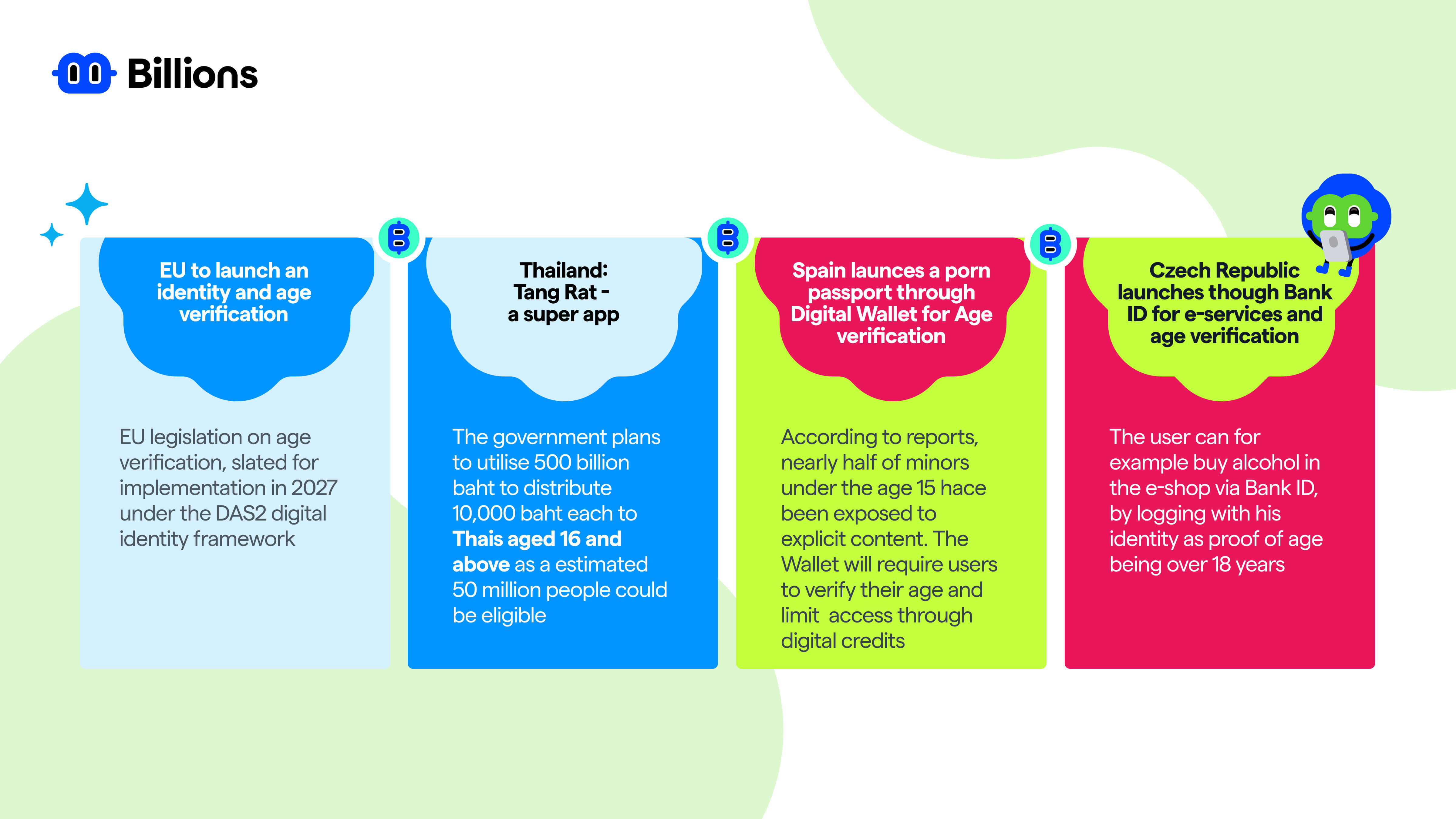
Digital identity age verification use cases and regulation around the globe
We see increasing initiatives related to digital identity being implemented across the globe. As a result, the regulations around digital identity are being deployed globally. In February 2026, Spain's Prime Minister Pedro Sanchez said "We will protect them (children) from the digital Wild West,". The announcement follows Australia's world-first social media ban for children under 16 finishing one month. Businesses have also started acting to remain compliant with regulation like Discord launched teen by default settings globally in Feb 2026
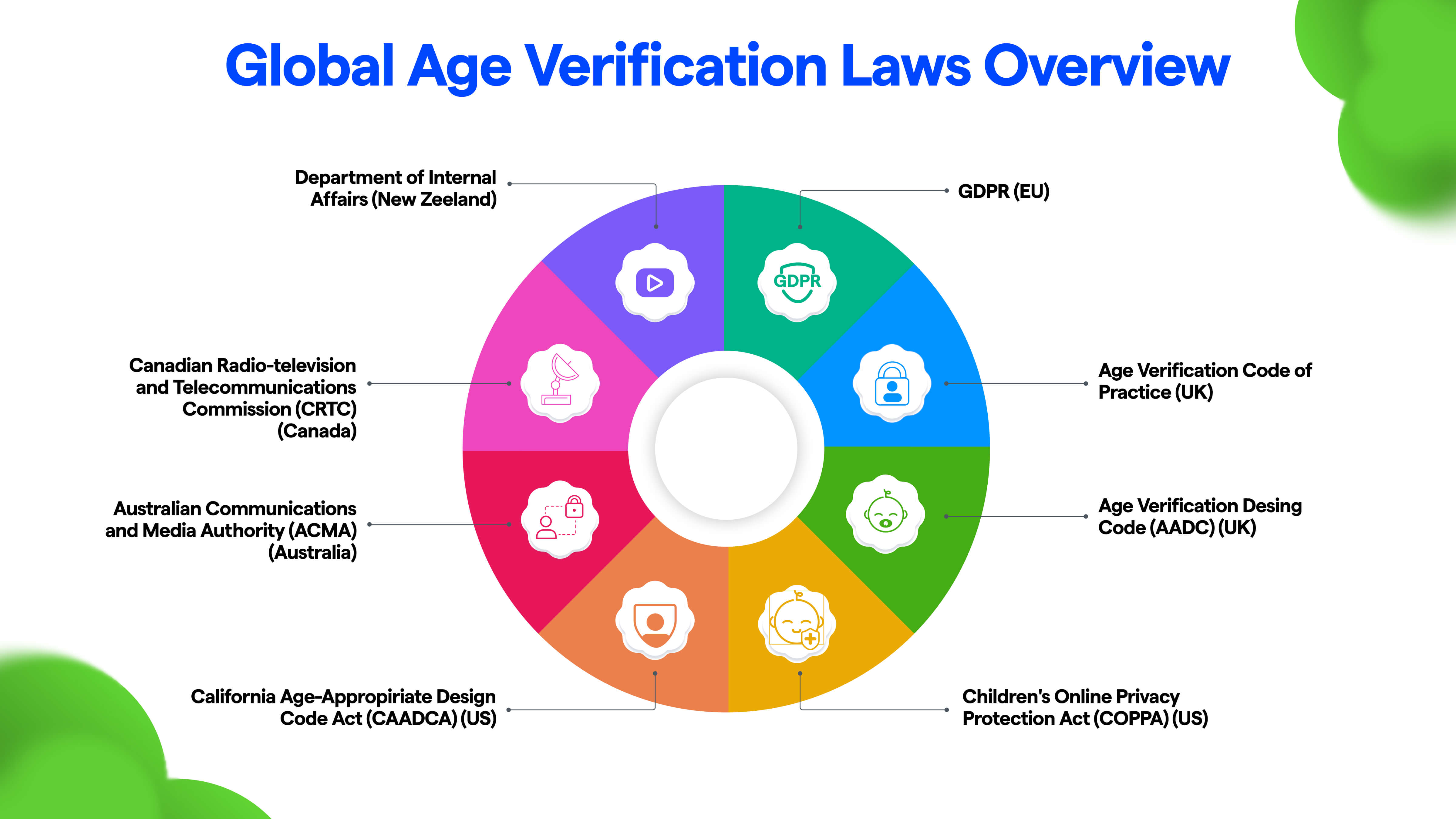
Solution for Digital Identity and Age Verification
Current issues with age verification:

Zero Knowledge Proof (ZKP) technology can solve these problems by guaranteeing privacy and reassuring users that both their data as well as their browsing history remain private and secure. Global regulation / investigations aiming to restrict access to certain content/ sites are increasing, along with financial (and criminal in some cases) penalties for non-compliance. These include multiple jurisdictions including the ones in Europe (Spain, France, and UK) and the USA (Louisiana, Utah, Texas, and several others).
Typical Age Verification Flow:
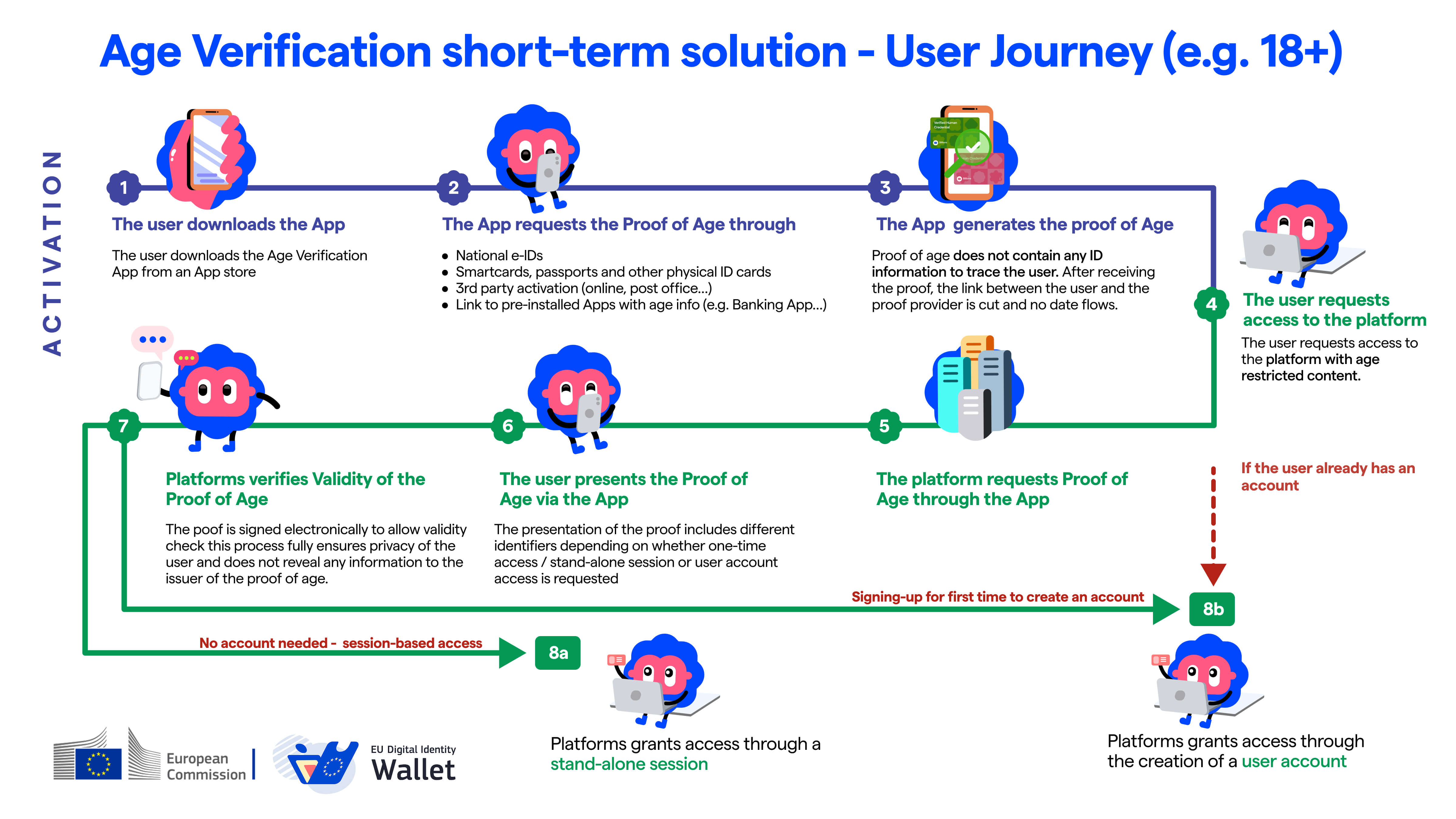
Billions Network’s Age Verification Solution
Billions Network’s solution enables an identity web wallet to store a “proof of age” verifiable credential. When the user attempts to access an age restricted site, the content site will set a query for the user to demonstrate that he is of appropriate age. The query is flexible, leveraging Billions Network’s zero knowledge query language, which means that the query could be of an age majority (age \> 18), but could also be a maximum age query (age \< 65\) or an age range query (age between 40 and 50).
The user can create the identity wallet by login-in with his email or a passkey on his own device. The user can obtain the credential from any of the authorized age verification providers in the open Billions Network ecosystem. This allows flexibility for a variety of age verification methods to be used (voice check, facial scan, id document scan, etc.)
Once the user has obtained the proof of age credential from the provider he is able to generate a ZK proof to demonstrate that a user has an appropriate age. The ZK proof is generated in response to the original query generated by the content site at the beginning of the process.
The verifier upon receiving the proof validates the correctness of the proof by running it through ZKP logic with only the public input values, as well as verifying that the credential has not been revoked by checking that Merkle tree proof is valid and comparing it to the issuer’s on-chain revocation tree. The proof can also be submitted to an on-chain verifier (smart contract) that will verify the validity of the proof received. This allows proofs derived from off-chain credentials to be used in on-chain interactions.
The verifiable credential data itself is off-chain, the only data on-chain are the issuer’s DID identifier and issuer state which reside in a Billions Network smart contract.
Usage of private and public keys
- Issuer public key: a claim of usage of this key is included via the issuer’s on-chain issuer state
- Issuer private key: used to sign the proof of age credential
- User public and private key: used in the creation of the identity wallet and also to derive the user did identifier
The Billions Network mechanism decouples the identity from the keys and allows for creation of additional identifiers (DIDs or profiles) and key rotation, which improves security (and is equivalent to periodically changing the lock on your front door).
Benefits of Age Verification:
Schema standardization with Industry leaders:
Interoperability is an essential feature for digital identity frameworks, considering the increasing trends of data sharing across networks. To meet these challenges, Billions Network is contributing to standardize the schema definition for age verification credential. This efforts are with several industry practitioners to make is consistent and simple for developers to integrate standard age proof in their application and expedite adoption
What data is stored in the “proof of age” credential?
The data fields in the proof of age credential include the following:
- Age range: minimum and maximum age
- Verification method used (voice, facial scan, document scan…)
- Probability of Correctness (%)
- Level of confidence: "asserted", "basic" (90%+), "standard" (99%+), "enhanced" (99.9%+) , and "strict" (99.99%+)
- Other credential metadata: Issuer identifier, expiration date.
Actors in the ecosystem:
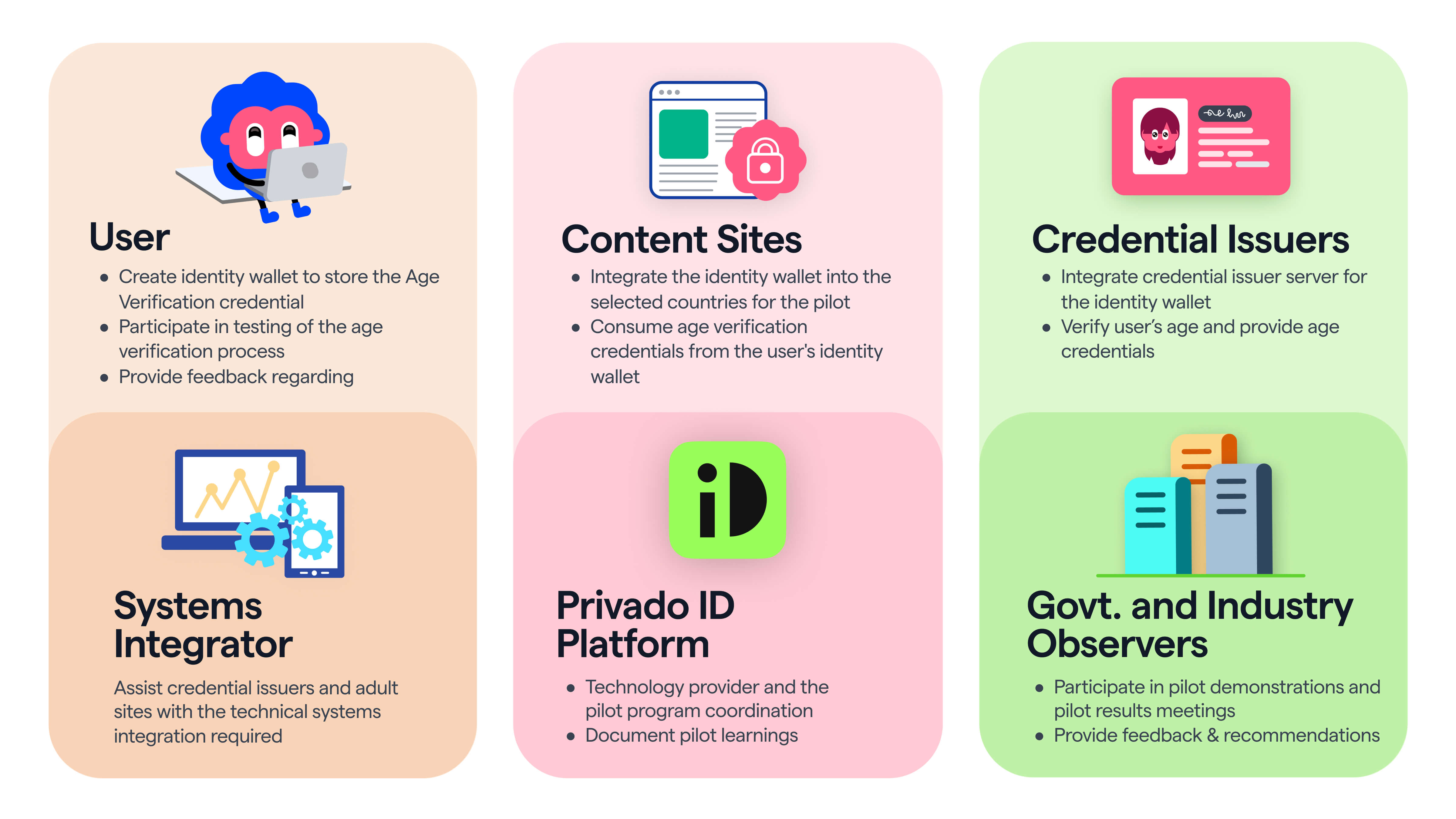
Conclusion
There is a rapidly evolving landscape in terms of regulations, with an increasing list of geographies opting for auditable and comprehensive age verification mechanisms. Also the growing regulations related to user and data privacy makes it mandatory for content providers to have an age verification solution. For the same reasons, it also makes sense to include age verification as an integral element of the digital Identity solution - a solution that ideally is available as a packaged solution, that can be deployed easily, reused across multiple use cases and can be seamlessly a part of the ever-increasing ecosystem of Digital Identity and its constituent participants.







